This command shows both static and shared loaded modules in Apache :
httpd -M
This command shows both static and shared loaded modules in Apache :
httpd -M
In order to flush all iptables rules , Run the following commands :
iptables -F iptables -X iptables -t nat -F iptables -t nat -X iptables -t mangle -F iptables -t mangle -X iptables -P INPUT ACCEPT iptables -P FORWARD ACCEPT iptables -P OUTPUT ACCEPT
In order to connect to a windows VPS remotely , you need to use a software named “Remote Desktop Connection” which is bundled with all versions of windows.
under windows XP it is located under : All Programs –> Accessories –> Communications
under windows Vista it is located under : All Programs –> Accessories
after running this software you will see the following window , enter the IP or host name of your VPS into the computer filed and click on Connect.
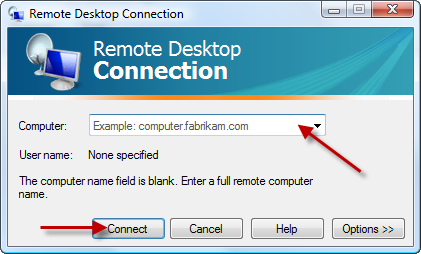
after a few seconds a new windows will be opened and you will be asked for the username and password , enter the username and password which is provided by your windows VPS provider. usually the username is Administrator.
if you enter the login details successfully , the desktop of windows VPS will be shown to you.
After you are logged into VPS , follow the below instructions :
Press CTRL+ALT+END buttons simultaneously , the following menu will appear :
Click on Change Password :
Fill the fields and click on OK.
Done 🙂
install libradiusclient-ng2 :
apt-get install libradiusclient-ng2
rename the folder :
mv /etc/radiusclient-ng/ /etc/radiusclient/
create dictionary.microsoft :
nano /etc/radiusclient/dictionary.microsoft
and copy and paste the following text into it :
# # Microsoft's VSA's, from RFC 2548 # # $Id: dictionary.microsoft,v 1.1 2002/03/06 13:23:09 dfs Exp $ # VENDOR Microsoft 311 Microsoft ATTRIBUTE MS-CHAP-Response 1 string Microsoft ATTRIBUTE MS-CHAP-Error 2 string Microsoft ATTRIBUTE MS-CHAP-CPW-1 3 string Microsoft ATTRIBUTE MS-CHAP-CPW-2 4 string Microsoft ATTRIBUTE MS-CHAP-LM-Enc-PW 5 string Microsoft ATTRIBUTE MS-CHAP-NT-Enc-PW 6 string Microsoft ATTRIBUTE MS-MPPE-Encryption-Policy 7 string Microsoft # This is referred to as both singular and plural in the RFC. # Plural seems to make more sense. ATTRIBUTE MS-MPPE-Encryption-Type 8 string Microsoft ATTRIBUTE MS-MPPE-Encryption-Types 8 string Microsoft ATTRIBUTE MS-RAS-Vendor 9 integer Microsoft ATTRIBUTE MS-CHAP-Domain 10 string Microsoft ATTRIBUTE MS-CHAP-Challenge 11 string Microsoft ATTRIBUTE MS-CHAP-MPPE-Keys 12 string Microsoft ATTRIBUTE MS-BAP-Usage 13 integer Microsoft ATTRIBUTE MS-Link-Utilization-Threshold 14 integer Microsoft ATTRIBUTE MS-Link-Drop-Time-Limit 15 integer Microsoft ATTRIBUTE MS-MPPE-Send-Key 16 string Microsoft ATTRIBUTE MS-MPPE-Recv-Key 17 string Microsoft ATTRIBUTE MS-RAS-Version 18 string Microsoft ATTRIBUTE MS-Old-ARAP-Password 19 string Microsoft ATTRIBUTE MS-New-ARAP-Password 20 string Microsoft ATTRIBUTE MS-ARAP-PW-Change-Reason 21 integer Microsoft ATTRIBUTE MS-Filter 22 string Microsoft ATTRIBUTE MS-Acct-Auth-Type 23 integer Microsoft ATTRIBUTE MS-Acct-EAP-Type 24 integer Microsoft ATTRIBUTE MS-CHAP2-Response 25 string Microsoft ATTRIBUTE MS-CHAP2-Success 26 string Microsoft ATTRIBUTE MS-CHAP2-CPW 27 string Microsoft ATTRIBUTE MS-Primary-DNS-Server 28 ipaddr Microsoft ATTRIBUTE MS-Secondary-DNS-Server 29 ipaddr Microsoft ATTRIBUTE MS-Primary-NBNS-Server 30 ipaddr Microsoft ATTRIBUTE MS-Secondary-NBNS-Server 31 ipaddr Microsoft #ATTRIBUTE MS-ARAP-Challenge 33 string Microsoft # # Integer Translations # # MS-BAP-Usage Values VALUE MS-BAP-Usage Not-Allowed 0 VALUE MS-BAP-Usage Allowed 1 VALUE MS-BAP-Usage Required 2 # MS-ARAP-Password-Change-Reason Values VALUE MS-ARAP-PW-Change-Reason Just-Change-Password 1 VALUE MS-ARAP-PW-Change-Reason Expired-Password 2 VALUE MS-ARAP-PW-Change-Reason Admin-Requires-Password-Change 3 VALUE MS-ARAP-PW-Change-Reason Password-Too-Short 4 # MS-Acct-Auth-Type Values VALUE MS-Acct-Auth-Type PAP 1 VALUE MS-Acct-Auth-Type CHAP 2 VALUE MS-Acct-Auth-Type MS-CHAP-1 3 VALUE MS-Acct-Auth-Type MS-CHAP-2 4 VALUE MS-Acct-Auth-Type EAP 5 # MS-Acct-EAP-Type Values VALUE MS-Acct-EAP-Type MD5 4 VALUE MS-Acct-EAP-Type OTP 5 VALUE MS-Acct-EAP-Type Generic-Token-Card 6 VALUE MS-Acct-EAP-Type TLS 13
create port-id-map in case it doesnt exists :
echo "" > /etc/radiusclient/port-id-map
edit /etc/radiusclient/dictionary :
nano /etc/radiusclient/dictionary
and add the following lines to the end of it :
INCLUDE /etc/radiusclient/dictionary.merit INCLUDE /etc/radiusclient/dictionary.microsoft
edit /etc/radiusclient/radiusclient.conf :
nano /etc/radiusclient/radiusclient.conf
copy and paste the following text into it , dont forget to set your own authserver and acctserver:
auth_order radius login_tries 4 login_timeout 60 nologin /etc/nologin issue /etc/radiusclient/issue authserver AUTH_Server_IP:PORT acctserver ACCT_Server_IP:PORT servers /etc/radiusclient/servers dictionary /etc/radiusclient/dictionary login_radius /usr/sbin/login.radius seqfile /var/run/radius.seq mapfile /etc/radiusclient/port-id-map default_realm radius_timeout 10 radius_retries 3 login_local /bin/login
edit /etc/radiusclient/servers :
nano /etc/radiusclient/servers
and add the following text into it , change Radius_Server_IP and SecretKey to your own settings :
Radius_Server_IP SecretKey
edit /etc/pptpd.conf :
nano /etc/pptpd.conf
and copy and paste the following text into it , change Server_IP , Remote_IP_From and Remote_IP_TO to your own settings :
option /etc/ppp/pptpd-options logwtmp localip Server_IP remoteip Remote_IP_From-Remote_IP_TO connections 200
edit /etc/ppp/pptpd-options :
nano /etc/ppp/pptpd-options
and copy and paste the following text into it :
name pptpd require-pap ms-dns 8.8.8.8 ms-dns 8.8.4.4 proxyarp nodefaultroute lock nobsdcomp mtu 1200 mru 1200 plugin radius.so plugin radattr.so lcp-echo-failure 50
install libpam-radius-auth
apt-get install libpam-radius-auth
open /etc/pam_radius_auth.conf
nano /etc/pam_radius_auth.conf
and add the following lines into it. Your_IP and PORT are the IP address and Port of Radius sever. SecretKey is the Secret of radius server. 3 is the timeout in seconds.
# server[:port] shared_secret timeout (s) YOUR_IP:PORT SecretKey 3
Change the permissions :
chown root /etc/pam_radius_auth.conf chmod go-rwx /etc/pam_radius_auth.conf
open /etc/pam.d/common-auth :
nano /etc/pam.d/common-auth
and add the following lines :
auth sufficient pam_radius_auth.so
I was getting this error on my openvpn server : read UDPv4 [EHOSTUNREACH]: No route to host (code=113)
it seemed to be a network problem , but after a lot of work I found out it is because the time and date of the client side was out dated !
if you are having the same problem please read this post : http://www.adminsehow.com/2009/06/how-to-synchronize-linux-time-daily/
DirectAdmin guide only asks you to download their setup script and run it , but it doesn’t explain about requires packages before installation , so before installation run the following commands :
yum update yum install perl gcc gcc-c++ make tar gzip bzip2 diffutils dbus quota
locate and updatedb commands are the best commands to search and find files in Linux. if you dont have them installed on your Linux , use the following commands :
Debian :
apt-get install locate
CentOS :
yum install mlocate
In order to integrate WHMCS 4.x with Jrox Affiliate Management (JAM) system , create a file named jam.php in whmcs/includes/hooks with following content :
<?
function actionhook_InvoicePaid($vars) {
if (!empty($_COOKIE['jrox'])){
$result=mysql_query("SELECT * FROM tblorders WHERE invoiceid = '".$vars."' LIMIT 1");
$row = mysql_fetch_array($result);
$JAMIntegrate = file_get_contents("http://www.domain.com/affiliates/sale.php?amount=".$row['amount']."&trans_id=".$vars."&custom_mid=".$_COOKIE['jrox']);
}
}
add_hook("InvoicePaid",0,"actionhook_InvoicePaid","");
?>
Make sure to point www.domain.com/affiliates to your JAM installation URL.
Powered by WordPress