As I have received several requests from Iranian readers of my blog, I have done some analysis on recent DigiNotar security breach and MITM attack to Iranian users.
This analysis is based on Fox-IT interim report of breach. You can download the complete report in PDF Format from the following link :
http://www.adminsehow.com/wp-content/uploads/2011/09/rapport-fox-it-operation-black-tulip-v1-0.pdf
What is MITM attack and how to prevent it ?
MITM stands for Man-In-The-Middle. it simply means someone stands between you and destination and intercepts or modifies your communication. it is quite easy when communication is not encrypted.
SSL protocol is originally invented to address this issue. The idea is that a trusted Authority (CA) authenticates the identity of destination and by using some cryptography protocols your connection to authentic destination becomes encrypted and impossible to intercept or modify.
It has been shown that the cryptography methods like AES or RC4 which are employed to encrypt the data are quite effective and very hard to crack. so the easier solution is to attack the base of trust model, the trusted authorities (CA). In this kind of attacks, hackers break into CA systems and forge valid certificates for themselves so they can impersonate themselves as authentic destinations and intercept the data. this kind of attack is used in both recent incidents, Commodo and DigiNotar.
Although the protocol is almost safe itself, unfortunately many of these CAs are vulnerable themselves making the whole process vulnerable.
The FOX-IT report indicates the DigiNotar systems were using Windows (Which is vulnerable in nature) and passwords has been crackable through brute-force attack. (More on this later)
To understand it better, I have created a diagram of recent MITM attack to Iranian users with the goal of intercepting communications between them and Google. the attackers have been able to gain access to Google accounts of users through this attack :
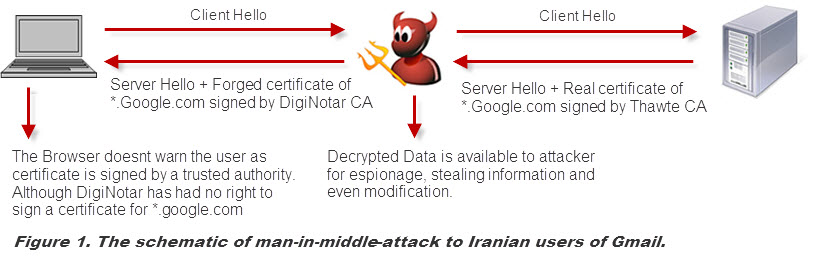
This diagram is self-explanatory. The attacker in middle impersonates itself as Google and establishes a secure connection to the user which is signed by DigiNotar CA. Although the connection is still secure, but users have a secure connection to the attacker, not real Google. so attacker has access to all information sent by user, including username, passwords, cookies and etc.
(more…)